Value Creation: Risk Management
Risks can be internal or external. Internal risk factors are those that a particular company may be subject to. A standard internal risk factor that small businesses face is critical person risk, where a company relies too heavily on a single individual or a small number of individuals. Risk mitigation can be achieved through several strategies so business owners can be proactive rather than reactive in handling risks present in their business.
We commonly pose the question to business owners, “What would happen to your business tomorrow if you got hit by a bus?” The answer may not be a complete implosion, but the consensus is business owners are too involved in daily operations.
External risk factors are those that all companies are subject to. There are some methods to reduce the risk of external risk factors, such as property insurance (natural disasters) or having a solid balance sheet to defend against a recession.
We suggest that business owners focus on managing internal risk factors rather than external ones, as the management team’s control is much higher.
Risk Management Framework
Every organization’s management team should adopt risk management. The most accepted framework involves four steps in the risk management world, including risk identification, risk analysis, severity assessment, and risk mitigation.
Step 1: Risk Identification
The first step of the risk management framework, risk identification, involves identifying all risk factors present in a company. This step of the framework should include the executive team, advisors, and representatives from different departments. Remember, the goal here is to account for all operational risks present in a business. Failure to include certain personnel could leave a risk uncovered. Lastly, while the focus in risk management is internal risks, it is essential to track external risks, as some of these risks can be mitigated.
Step 2: Risk Analysis
The second step of the risk mitigation framework, risk analysis, involves assessing the severity or impact of the risk and the probability of the risk occurring. As with the first step of the framework, this step should be done as a team. When assessing the impact of a risk factor, considerations such as cost and performance should be at the forefront of the team’s risk analysis. Take, for example, CyberCo, a business going through the Risk Management Framework. During the risk analysis step, a member of CyberCo’s team shared their findings on the revenue breakdown from customers. They noticed that an individual customer accounted for 20% of revenue. If CyberCo loses this customer, a huge chunk of revenue has been reduced to nothing. Luckily for CyberCo, their team analyzed the probability of this coming to fruition and realized it was very unlikely to occur.
Step 3: Risk Priotiziation
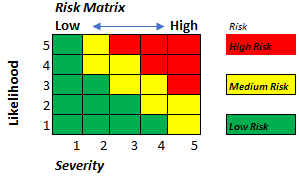
The third step of the risk mitigation framework, risk prioritization, involves weighing each risk in order of importance based on the risk analysis done in step two. A common way to visualize which risk factor to focus on first is through a risk management matrix. Using a risk management matrix, different sections are allocated to low, medium, and high-risk factors. Each risk factor is then plotted on the matrix and allocated to other color-coded quadrants that correspond to a risk level. An example of a risk management matrix is shown below:
Step 4: Mitigation, Planning, Implementation, and Progress Monitoring
The fourth step of the Risk Mitigation Framework, risk mitigation, planning, implementation, and progress monitoring, uses a risk mitigation strategy to lower risk. Risk factors should be addressed based upon the risk prioritization done in step two. It is also essential to keep track of all risk factors in your backlog, as ebbs and flows in your business can exacerbate a previously determined low-to-medium prioritized risk into a high-level risk.
The Five Risk Management Strategies
Five risk mitigation strategies are commonly used in risk management, including assuming and accepting, avoidance, control, transfer, and watch and monitor. There is no one-size fit all method of mitigating risk. Each strategy above can be deployed given the right circumstances.
#1: Assume and Accept
The first risk mitigation strategy, assume and accept, involves acknowledging the existence of a risk and accepting its repercussions. This may seem like a bad strategy. However, if a risk is unlikely to occur along with a low impact, it may be appropriate to accept the risk and focus on other business areas. Consider the opportunity cost of the situation: time spent on reducing the risk of something that would have a minimal impact on a business is simply inefficient. Back to CyberCo, consider its reliance on a single vendor but with alternates available. Given that CyberCo can switch vendors with relative ease and minimal disruption to operations, spending time altering its supply chain would slightly improve its risk profile. Instead, CyberCo should accept this risk and focus on other risks in its business.
#2: Avoidance
The second risk mitigation strategy, avoidance, involves operating to limit a risk entirely by avoiding it together. Take the popular reality TV show Shark Tank, for example. The Sharks regularly choose to turn down certain ventures. Why? The Sharks analyze each business idea to understand its potential risk versus return. Some investments may be worth the risk, and the Sharks are willing to accept that risk (assume and accept), and other ventures are just too risky (or just plain wrong ideas…) and are turned down without blinking an eye.
Similarly, a management team might be considering starting a new product line. After a consumer analysis, the data is not convincing enough that the product will be successful from profitability. The management team decides to forgo the initiative, and in the process, avoiding the risk entirely.
#3: Control
The third risk mitigation strategy, control, involves creating an action plan to reduce the severity or probability of a risk occurring. The control risk mitigation strategy can be used when a risk factor has a high likelihood of occurring and high financial impact. It is common for a company to double or even triple its revenue in the government contracting space by winning a single, large contract. Scaling up quickly, however, has its challenges. For example, a company must hire additional staff and possibly secure a credit line to facilitate this growth. Using the control risk mitigation strategy, businesses anticipating accelerated growth might invest in staff proactively, improve onboarding processes, and move their HR function in-house.
#4: Transfer
The fourth risk mitigation strategy, transfer, involves assigning the risk from one party to another. Most small businesses already partake in this type of risk mitigation strategy through insurance. General liability insurance, commercial property insurance, and worker’s compensation insurance are all common forms of insurance businesses have.
Another form of transfer as a risk mitigation strategy is through indemnification provisions in contracts. Such provisions are common with construction firms, where a subcontractor agrees to be liable for any issues that may arise of their own doing.
#5: Watch and Monitor
The final risk mitigation strategy, watch and monitor, involves adjusting a risk management plan as required. Recall that risk in your business ebbs and flows over time. Risk factors that may have been categorized in the low to the medium range may change. For example, perhaps alternate suppliers of CyberCo went out of business. CyberCo’s previous assessment of its reliance on its key vendor is not current, implying severe operational disruption in its supply chain. CyberCo must then transition from assuming and accepting this risk to actively controlling it. As such, watch and monitor should be at the forefront of every business’s risk management strategy.
Wrapping Up
Risk Management is a crucial part of any business owner’s long-term strategy. Value creation is possible by focusing on increasing earnings, achieving growth, and managing risk. A business owner cannot achieve the latter without an active risk management plan in place.